Tarah Wheeler's Blog
November 17, 2025
A Cenotaph for Internet Freedom: Reviewing “Geopolitics at the Internet’s Core”
At first glance, Geopolitics at the Internet’s Core (Amazon affiliate link) by Fiona M. Alexander, Laura DeNardis, Nanette S. Levinson, and Francesca Musiani reads as a dense technical history of Internet Protocol—that constellation of technical specifications and social agreements that makes the internet work. But this would be a profound misreading.
What Alexander, DeNardis, Levinson, and Musiani have actually written is something far more elegiac: a cenotaph for a bygone era of consensus and freedom, created by the nerds who midwifed the internet into existence.
The Hidden WarBeneath the surface of our everyday digital lives, a quiet war rages over the technical specifications of the internet. This conflict plays out in regulatory bodies and standards-setting organizations, and it disturbingly mirrors—sometimes even precedes—kinetic conflicts in the physical world. Chinese feints, European collective action problems, wild swings in US power and support for allies, Russian criminal activity: the politics of internet governance function as a preview of coming attractions.
For those of us embedded in this world, one of the book’s most fascinating revelations is the documentation of Chinese attempts to shift standards-setting from the IETF (Internet Engineering Task Force) to the ITU (International Telecommunication Union). This isn’t just bureaucratic musical chairs. It’s a deliberate strategy to move the locus of control from a body that operates on “rough consensus and running code” to one that is essentially moribund. I think the motivation here is clear: institutional deadlock opens the global game for subversive disruption.
From Borderless Bits to Westphalian InternetThere is a fundamental mismatch between borders and bits—between the laws governing political entities and the decentralized, cross-border way information actually flows. I’ve discussed this before when the state government of Montana tried to ban TikTok. The book traces how this tension has evolved from an idealistic dream of a universal internet to our current reality: an increasingly fragmented network where the internet looks different depending on what country you’re in.
Rather than the “three internets” framework I’ve previously argued for, the authors make a more powerful—and more pessimistic—case: we are walking backwards toward a Westphalian internet. Nation-states are reasserting sovereignty over digital space, carving up the once-unified network along the same territorial lines that have governed physical space for centuries.
This is the book’s most powerful argument, and it should alarm anyone who cares about the future of global connectivity.
Technical Infrastructure as Political Power“Technical infrastructure [is] a proxy for political power.” This observation, buried in the book’s analysis of IP address allocation controversies, encapsulates its core thesis. The seemingly neutral technical choices made by engineers—often thoughtlessly, without considering how humans actually wield power—have become battlegrounds for geopolitical competition.
The book excels at translating between two communities that desperately need to understand each other. For policymakers, it demystifies the technology of IP addressing, routing protocols, and internet governance. For technical experts, it explains why politics are happening to the internet, and why the architecture they built is now a contested space.
Where the Book StumblesThe text does suffer from some repetitiveness, likely a function of its four authors. Multiple similar explanations of 32-bit IPv4 addresses appear throughout, for instance. But these redundancies do less harm than one might expect—they’re speed bumps rather than roadblocks, and it’s an incredibly important concept to understand the rest of the book.
Why This MattersWhat makes this book essential reading is its translation work. It bridges the gap between technical and policy communities at a moment when that bridge has never been more critical. The engineers who built the internet’s core protocols made decisions that seemed purely technical at the time. They couldn’t foresee—or chose not to consider—how their architectural choices would become instruments of state power, tools of surveillance, and mechanisms of control.
The book chronicles three major struggles in IP’s history: the foundational battle between TCP/IP and OSI protocols, the expansion struggle over IPv6, and the twenty-year control struggle that ended with the 2016 IANA stewardship transition. Each of these seemingly arcane technical debates actually determined fundamental questions about who controls the internet and how power flows through digital space.
The StakesAs the authors warn in their conclusion, the societal stakes will only increase as digital networks embed further into humans, objects, financial systems, and medicine. The Internet Protocol has endured for decades through what economists call “long cycles”—extended periods of stability punctuated by turbulent transitions. We may be approaching another such punctuation point.
The question isn’t whether the internet will remain important. It’s whether it will remain the internet—a single, interoperable network—or fracture into a collection of sovereign digital territories. The geopolitical pressures documented in this book suggest the latter outcome is increasingly likely.
Geopolitics at the Internet’s Core memorializes a moment when the internet’s governance reflected the ideals of its founders: open, decentralized, built on rough consensus. That moment is passing. What comes next depends on whether we heed the lessons this book has to teach.
For anyone working in technology policy, internet governance, or who simply wants to understand the hidden political dimensions of the infrastructure we depend on daily, this book is indispensable. It’s dense, occasionally repetitive, but ultimately necessary. The war over the internet’s soul is being fought in standards bodies and routing tables. This book is your field guide to that battlefield.
Here’s an Amazon affiliate link to the book: https://amzn.to/4oQnmHC
August 13, 2025
Proactive Defense: Iranian Cyber Threats and How to Push Back
Public and private organizations across the United States, especially those with ties to critical infrastructure, are under increasing pressure from Iranian cyber actors after the events of weeks ago. The reality of the initial event and the impact on cybersecurity over the next few months is still being determined. While it is easy to say that the impact on commercial entities is over, the reality is that the Iranian nation-state attackers will continue to act at a higher and more focused rate. Focusing on Critical infrastructure and supply chain attacks that will disrupt everyday life. If you have many of the security checklist items discussed in this article completed, you only have a slightly elevated risk due to these events. These threats aren’t theoretical. They’re calculated and persistent, often starting with the most basic security gaps: stolen credentials, unpatched systems, and weak email hygiene. What makes this more dangerous is that many of these businesses don’t realize how attractive they are as stepping stones in larger supply chain attacks. They think that they’re “too small to be interesting.” Nation-state threat actors are overwhelmingly concerned with collecting intelligence. While you may think your organization has nothing of intelligence value, one of the networks to which you’re connected may. Nation-state threat actors typically follow the path of least resistance to achieve their intelligence objectives. While this may seem overstated and a bit of staged drama, it isn’t. We must be clear that nation-state actors are targeting critical infrastructure and other key interests every day. One of the most important but technically unsophisticated US critical sectors is agriculture, and US food production is under an increased threat of cyberattack. Air travel has been the focus of Iran and cybercriminals allegedly working on behalf of Iran over the last month. Still, it is the third major US business sector in the last two months, after insurance and retail, to face a flurry of cyberattacks tied to the Iranian nation-state.
Iranian attackers rely on simplicity and scale. One of the most common and simple ways for any attacker to quickly find credentials is spearphishing. This particular attack calls for a bit of research on LinkedIn and selecting a target based on their role and connectivity to the targeted system, not their seniority. This means using some basic confidence scams to gain access to credentials or applications that allow for credential harvesting. Commonly, this credential is reused through credential stuffing, phishing, and social engineering, and these inexpensive, low-skill attacks provide an excellent return on investment. Many organizations still don’t provide consistent email protection or user training, which makes phishing the path of least resistance and highest value.
Rather than running elaborate simulations, organizations should consider sending a simple, real-world message to their staff about the current threat. Share examples, give context, and focus on building awareness. Avoid the trap of ‘test’ phishing campaigns that can inadvertently encourage users to click more often; there is no industry-accepted proof that trap phishing campaigns improve digital security, and peer-reviewed studies show that they decrease employee morale and loyalty. Once credentials are harvested, attackers often spray passwords or conduct brute-force attacks against known services like VPNs, Outlook Web Access, or internal portals. This is where multi-factor authentication (MFA) plays a critical role. However, not all MFAs are created equal. The MFA solution you choose should have an out-of-band fallback, which means that in the event of an attack or failure, the MFA system should not fail to an internal tool, but rather to an external communication tool like Slack, Email, SMS, or Voice Calls, to force the attacker to compromise multiple separate systems at once. Iranian actors have adopted “push bombing,” where users are overwhelmed with MFA prompts until they approve one out of fatigue. Organizations should enforce phishing-resistant MFA, set sensible rate limits on login attempts, and include this in security education sessions. Teaching users not to approve repeated prompts is essential.
Another major avenue of attack is unpatched infrastructure. Iranian threat actors have a strong track record of exploiting known vulnerabilities in edge devices, servers, and cloud configurations. The best countermeasure here is disciplined patching, paired with clear visibility into your deployed systems. Vulnerability management has to be a shared responsibility between your development, IT, and security teams. This goes beyond simply installing updates; it requires understanding how vulnerabilities interact with your environment and risk posture. If you do not have a combined average metric for time-to-patch in each of the five Critical/High/Medium/Low/Informational categories of vulnerability, this is the moment to start doing so and making it a shared responsibility across IT and infosec.
There is also growing concern over ransomware and destructive attacks. While many associate ransomware with financial gain, Iranian groups have demonstrated a willingness to use destructive tools, such as wipers, to erase data and permanently conceal the traces of their operations. The reality is that paying the ransom, especially when facing a nation-state actor, is unlikely to restore your data. A more effective strategy is to invest in backup integrity and disaster recovery testing. You must know how quickly you can recover from a full system wipe, not just a data encryption scenario, and that means testing your capacity to recover from a full production outage, not simply updating your playbooks.
Defensive architecture begins with understanding who and what you’re defending, and determining identity and access. It’s essential to enforce strong passwords, limit access rights through the principle of least privilege, and monitor privileged accounts closely and systematically. Identity is the new perimeter. Iranian campaigns have repeatedly targeted weak identity infrastructures because once inside, they can escalate privileges and access broader resources. We also can’t ignore the human threat. Iranian campaigns have occasionally leveraged insiders, whether directly recruited or socially engineered. We are beginning to see spearphishing versus an unexpected target: not the CEO or CFO, but the admin in control of the IAM application inside organizations. Insider risk isn’t just about detection; it’s about prevention. Device encryption (via tools like BitLocker or FileVault), MDM enforcement, and tight offboarding procedures are baseline expectations. These controls must be complemented by clear HR coordination and periodic audits of access entitlements. Be aware that unexpected people in your organization may become targets of the kind of sophisticated social engineering to which only the C-suite was previously subject.
Endpoint protection matters. Endpoint Detection and Response (EDR), mobile device management (MDM), and secure virtual private network (VPN) practices are essential. Many employees still connect to corporate networks via home devices and unsecured networks, creating a soft path for attackers. Organizations should monitor endpoint behavior, enforce regular updates, and isolate unmanaged devices. Similarly, understanding DNS activity across your network, internally and at the edge, provides early signals of command-and-control or data exfiltration attempts.
Network segmentation is another powerful layer of defense. The days of wide-open LANs with shared access to all systems are long gone. Break your network into segments, restrict access by role and function, and use firewalls and monitoring tools to maintain visibility and control. If you operate industrial control systems (ICS) or operational technology (OT) systems, they should never be exposed to the internet directly. Take the time to finish your segmentation effort and document it fully. Cloud infrastructure must be treated with the same rigor. Whether you use AWS, Microsoft 365, or Google Workspace, make sure your deployment follows platform-specific security best practices. Cloud doesn’t remove responsibility; it shifts it. Use the AWS Well-Architected Framework, Microsoft Secure Score, and Google’s Cloud Security Foundations to continuously evaluate your posture.
None of this works without good governance. Policies should explicitly mandate the use of MFA, define acceptable use, and require regular access reviews. Governance documents aren’t just compliance tools- they’re operational guides. They define expectations and enable accountability. Alongside this, tabletop exercises help teams internalize those policies. By simulating attacks and walking through responses, you uncover real weaknesses in your playbooks, staffing models, or communication plans. All of this ties back to a single theme: risk-based prioritization. Not every asset needs Fort Knox protections, but some do. The problem is, most organizations don’t know which of their assets are critical. Reassess regularly. Understand where you fit in your industry’s supply chain. If your compromise would enable access to others, you’re not a soft target- you’re a strategic one.
Finally, look to established frameworks to guide you. The National Institute of Standards and Technology (NIST)Cybersecurity Framework (CSF), along with NIST 800-53 and NIST 800-171, offer strong starting points for defense and control design. The goal isn’t perfecting IT resilience. Iranian attackers will continue their campaigns. It is far easier to prepare than to clean up. In many cases, these tasks are things you would or should have done anyway.
Top 3 Checklist for Iranian Threat DefenseImplement phishing-resistant MFA and rate-limit login prompts to prevent fatigue-based approval. This is table stakes. You and everyone in your organization must use MFA, and failure to do so must be referred to HR. MFA is often seen as a barrier to “getting work done,” but as long as there’s a fallback method that is out-of-band for your organization and well-tested, there are no longer any excuses.The attacker is focused on low-cost human failures because humans are easy to manipulate. Focus on spearfishing and whaling in LinkedIn, email, and other communication sources. Don’t assume that because they don’t always use a technical attack, they are not technically competent. This attacker focuses on a simple method with a good return margin, so consider this like a financial transaction, and quantify your risk in that light.IT and infosec hygiene is the single most important area. Ensure your logging is enabled, have devices screenlock, etc. They’re looking for low-hanging fruit. Don’t be embarrassed by techniques that should be too low-level to succeed against you; get your ducks in a row now. Appendix: Notes, Credits, and CitationsHistorical incidents: Shamoon, APT33, MuddyWater, ZeroCleareVendor frameworks: AWS Well-Architected, Microsoft Secure Score, Google Cloud Security FoundationsPassword Managers: Bitwarden, 1Password, KeePassXCAugust 7, 2025
Players! Welcome to the 4th Annual EFF Benefit Poker Tournament at Defcon 33!
Welcome! Here’s some info as we get ready to play! Come to the Planet Hollywood Poker Room at 11AM for the poker clinic with Mike Wheeler, and the tournament starts at noon. Our own Lintile will MC this year!
What should I bring? Consider getting your cash in hand from a convenient ATM and if you have one, your Caesars Reward card (physical card, can be gotten at any Rewards desk and most cages). This will prevent jam-ups from happening at the ATM right outside the poker room. You will need $100 in cash or Planet Hollywood Casino chips to register for the tournament. If you get knocked out and want to rebuy, it’ll be another $100 to rebuy into the tournament with a $100 additional suggested donation to the EFF.
Do I need photo ID? Yes, you have to have ID on you per the Nevada Gaming Commission. In addition, if you win money, the poker room will check it to pay you out at the end.
Where do I go? Come to the Planet Hollywood Poker Room inside the Planet Hollywood Casino either at 11AM Aug 9th if you want to do the clinic or a few minutes before noon Aug 8th if you’re coming for only the tournament. This is the same place it’s been for the last two years.
Do I need to check in? You have already donated $250 to the EFF, and your name will be on the checklist that Daniel De Zeeuw will be holding; check in with him when you arrive.
If I spot a friend along the way and they haven’t registered yet, can I drag them along with me and have them register on site? Yes, but please, please do register in advance if possible – we’re not going to turn people away but if we run out of dealer capacity it would suck to not have that additional warning and the donation to the EFF.
How much money should I bring with me? You will need $100 in cash to register for the tournament at the Planet Hollywood Poker Room front desk. You do not technically have to have a Caesars Rewards card to do this, but it makes it easier.
When is the poker clinic and who is it for? Dad and I are teaching the poker clinic from 11AM-12PM, just before the tournament starts. If you want that brush up on your table etiquette or any of the rules, this is that chance. It’s also something that really intimidates people, so if you have friends who want to play but are hesitant in case they’ll be a noob and wreck it for others, this is why we do this! This is a super warm and welcoming tournament.
Do I need to tip my dealers? In a tournament, it’s not usual to tip your dealers, as the winner of the tournament is expected to tip about 10% of their winnings to the winning dealer, who will tip out the rest of the staff. However, it would be very kind to tip any dealer you think does a great and kind job of helping players enjoy themselves. This is an…odd tournament for them and most of the dealers are not used to very friendly people who aren’t (at least in the first stages of the tournament) as competitive as they are inquisitive. Dropping a dealer a fiver is a nice gesture.
Will I be seated at a table with one of the celebrity guests? Probably. I’ll work to make sure they’re evenly distributed this year. Last year, I didn’t think to tell the poker room manager that it would be nice if the people I specified were broadly distributed, so we got a clump of celeb guests at one table. I’ll try to make sure that doesn’t happen. You may be moved from one table to another at the discretion of the poker room manager. That’s a thing that happens in poker tournaments; please be understanding and do what the poker room manager says to do. This is a Nevada Gaming Commission thing, not a thing I have control over. If you knock out a celebrity guest, they’ll likely be v happy to do pictures with you, and might even have something nifty for you as a present!
Can I rebuy? Rebuys will be permitted to the end of the break after round 6. They are $100 with a suggested additional donation of $100 to the EFF. Daniel will be able to help you with your rebuy donation, and the front desk will take your $100 for the tournament cost.
How long will the tournament go? We’ll start at noon. Usually rounds are 15 minutes. In my experience, the tournament will go for about 9-10 rounds; it is very quick. The final table will probably not last more than 45 minutes. We will probably be out of there even after last pictures and prizes no later than 3:45PM.
If I win, how do I get paid out? If you are one of the players who will get paid at the end of the tournament (usually between 4-8 people or so), the poker room will give you a payout slip to take to a cage or they’ll pay you out in cash right there, depending on what they have on hand.
Can I make prop bets? Yes! Prop bets, or proposition bets, are like the side bets you can make. A really common prop bet is a “last longer” bet, where two or more people will bet a certain amount into a pool on who will last longer in a tournament, and the winner collects the kitty. An example of a prop bet is where I donate $250 to the EFF in the name of whoever knocks my father out of the tournament! Lintile will help you out with this!
What’s the photo policy? You’re in a public area absolutely saturated with video surveillance and everyone is loaded for bear on camera equipment, so consider that a photo of you may happen accidentally. In general there will be photos being taken; this is an event intended to be publicized for the EFF and shiny happy faces on the fediverse means more cash for hackers. However, if you do not want your photo taken, you are ABSOLUTELY welcome to say so, no one will be upset at you or think less of you, and the EFF will have “No Photos” stickers you can wear, meaning that people will see that and all will do their best to blank your face and not show you.
Can I bring a friend who isn’t going to play but who wants to watch? Sure. They may be limited in how close to your table they can approach, based on where the other tables are, or what the other players are comfortable with, but you can sure bring them. Maybe encourage them to make whatever donation to the EFF they feel comfortable with?
Can I hack stuff at/near the poker room? No. Don’t get me in trouble with the Nevada Gaming Commission. Don’t scare the normies; they get cranky when they have thousands of dollars on the line and the LCDs around them start showing WarGames.
I have more questions! Nifty. Email events@eff.org. Can’t wait to see you there!
April 7, 2025
“Parental Units–we need to have The Talk.”
I just sat down with several of my family members, and gave them The Talk about how someone might call pretending to be me, and how voice and AI phishing filters work. Deviant and I have been getting family onto password managers to handle the more sophisticated attacks that are starting to pop up. Getting everyone onto password managers for everything is important but not urgent. That’s why it’s slipped on my todo list for literally years — and I also figured it would take some time and emotional energy to get family to operate differently. The juice is finally worth the squeeze to protect them all.
A random access memory gave me a good idea about how to start that conversation – just a single word. Many of us had a family password when we were little. I remember that there was a password for our family. It is still burned into my brain right along with my phone number and address from when I was a toddler. My parents could still use it and I’d know it was ok to get in a car with someone they sent. Start with that as a baseline.
If it seems overwhelming to start the conversation with especially aging family members about how to protect their financial assets and personal data, and how password managers are the best way to do that now, you can start with the talk about how AI vishing is growing extremely sophisticated and how you want to help them avoid it. Your cost for incident response for a true breach of multiple family member passwords to all financial accounts is going to be a devastating, months-long trauma for them and for you, as you work to not only help them, but must cope with their feelings of frustration and fear. It’s an *awful* IR scenario. We have been mostly fortunate to escape that so far, but I know some friends who have waited just a bit too long to start training family on how to handle online security and have seen finances, relationships, and futures irreparably damaged. This is important, but often gets backburnered. Start making the time now while you have trust and a bit of time.
A few technical lessons I learned about this process: first, don’t assume without a screen share session. One family member had a bad experience with 1Password that they hadn’t told me about. They grew frustrated typing in the long random passwords, and stopped using it in favor of Google Chrome’s password manager without understanding how they were storing multiple or problematic passwords. I hadn’t explained how to use 1P on a phone and computer, and I assumed they knew how to install the extension from the Chrome Web Store, and so forth. Don’t assume your family knows how to use a password manager. If you’re going to do this, make sure to walk your family through installing 1P onto both a phone and a computer (including the relevant browser extension), and how those passwords are shared in the cloud.
Next, explain carefully that there’s a difference between using the same password everywhere, and using a master password to access a vault which stores unique passwords. I have explained that it’s the difference between using a key only you have which opens a key cabinet, and using the same physical key for your office, car, and house. If someone steals a key to one of your possessions, at least they haven’t stolen the key to *everything*.
Follow up. Follow up. Follow up. Check back in with them quarterly and ask them to show you how they’re doing and ask if they have any problems with any browsers. Check their email multifactor authentication every time. Spend fifteen minutes a quarter for the rest of their lives. It’ll be worth it. Talking about it now will help, because in an emergency and with no context, it’s going to be very hard for family to process that you’re more experienced at technology and should be trusted. They’ll remember only that they wiped your nose and made your lunches. There are a lot of globally-recognized brilliant 45-year old cardiothoracic surgeons who have parents who will go to literally any other doctor, including a chiropractor or dentist–than their kid if they get chest pains. Start building trust and the conversation now, because the only thing worse than getting the IR call in the middle of the night is not getting it until someone else has royally screwed up the initial response.
Remember that family password? Think about it right now. Ask your family if they remember it…and I bet they do. I have a tall stack of hundred dollar bills that says that they *never* reused that password for anything else. Those family passwords were precious enough that they had a single word or phrase they never, ever reused for something as trivial as a bank account or email password, and they’ll instinctively understand that their vault password has to be as carefully safeguarded as the family password they used when giving a stranger mental access to their children. It’s the most powerful security analogy I know; if it will help you, use it.
October 20, 2024
A free, printable, editable cross-country planning form for VFR XC flight
Hi there! Searching the internet is impossible now, and all good content is locked up behind paywalls or subscriptions, so I’m releasing this freely. You can edit it if you want to in Acrobat or a similar PDF editing app. I’ve thrown this all up under the GPL.
VFR XC flight planning form as a PDF
Here’s the whole repository of my aviation resources.
Thank you to Deviant Ollam for gorgeous PDF edits! There’s also a version in the repo that has Washington state so I can mark areas for TFRs and NOTAMs, etc. An older version of this form was given to me by my friend Zachary Sherman, and he’s requested that I provide an acknowledgement to an aviator named Cyndy Hollman (sp?) who may have created the original version of this years ago.
August 6, 2024
Welcome to the EFF Benefit Poker Tournament at Defcon 32!
Welcome! Here’s some info as we get ready to play!
Nota bene: If you haven’t registered by now, please do so! I need to tell the poker room the expected number of players so they can allocate the correct number of dealers and so the EFF can estimate how many poker card decks to bring. If you have friends who intend to come who haven’t yet registered, please have them do so ASAP.
What should I bring? Consider getting your cash in hand from a convenient ATM and if you have one, your Caesars Reward card (physical card, can be gotten at any Rewards desk and most cages). This will prevent jam-ups from happening at the ATM right outside the poker room. You will need $100 in cash or Horseshoe Casino chips to register for the tournament. If you get knocked out and want to rebuy, it’ll be another $100 to rebuy into the tournament with a $100 additional suggested donation to the EFF.
Do I need photo ID? Yes, you have to have ID on you per the Nevada Gaming Commission. In addition, if you win money, the poker room will check it to pay you out at the end.
Where do I go? Come to the Horseshoe Poker Room inside the Horseshoe Casino either at 11AM Aug 9th if you want to do the clinic or a few minutes before noon Aug 9th if you’re coming for only the tournament. This is the same place it’s been for the last two years.
Do I need to check in? You have already donated $250 to the EFF, and your name will be on the checklist that Daniel De Zeeuw will be holding; check in with him when you arrive.
If I spot a friend along the way and they haven’t registered yet, can I drag them along with me and have them register on site? Yes, but please, please do register in advance if possible – we’re not going to turn people away but if we run out of dealer capacity it would suck to not have that additional warning and the donation to the EFF.
How much money should I bring with me? You will need $100 in cash to register for the tournament at the Horseshoe Poker Room front desk. You do not technically have to have a Caesars Rewards card to do this, but it makes it easier.
When is the poker clinic and who is it for? Dad and I are teaching the poker clinic from 11AM-12PM, just before the tournament starts. If you want that brush up on your table etiquette or any of the rules, this is that chance. It’s also something that really intimidates people, so if you have friends who want to play but are hesitant in case they’ll be a noob and wreck it for others, this is why we do this! This is a super warm and welcoming tournament.
Do I need to tip my dealers? In a tournament, it’s not usual to tip your dealers, as the winner of the tournament is expected to tip about 10% of their winnings to the winning dealer, who will tip out the rest of the staff. However, it would be very kind to tip any dealer you think does a great and kind job of helping players enjoy themselves. This is an…odd tournament for them and most of the dealers are not used to very friendly people who aren’t (at least in the first stages of the tournament) as competitive as they are inquisitive. Dropping a dealer a fiver is a nice gesture.
Will I be seated at a table with one of the celebrity guests? Probably. I’ll work to make sure they’re evenly distributed this year. Last year, I didn’t think to tell the poker room manager that it would be nice if the people I specified were broadly distributed, so we got a clump of celeb guests at one table. I’ll try to make sure that doesn’t happen. You may be moved from one table to another at the discretion of the poker room manager. That’s a thing that happens in poker tournaments; please be understanding and do what the poker room manager says to do. This is a Nevada Gaming Commission thing, not a thing I have control over. If you knock out a celebrity guest, they’ll likely be v happy to do pictures with you, and might even have something nifty for you as a present! Our MC is Cory Doctorow, and our three other celeb guests are Runa Sandvik, Deviant Ollam, and MalwareJake Williams!
Can I rebuy? Rebuys will be permitted to the end of the break after round 6. They are $100 with a suggested additional donation of $100 to the EFF. Daniel will be able to help you with your rebuy donation, and the front desk will take your $100 for the tournament cost.
How long will the tournament go? We’ll start at noon. Usually rounds are 15 minutes. In my experience, the tournament will go for about 9-10 rounds; it is very quick. The final table will probably not last more than 45 minutes. We will probably be out of there even after last pictures and prizes no later than 3:45PM.
If I win, how do I get paid out? If you are one of the players who will get paid at the end of the tournament (usually between 4-8 people or so), the poker room will give you a payout slip to take to a cage or they’ll pay you out in cash right there, depending on what they have on hand.
Can I bring a friend who isn’t going to play but who wants to watch? Sure. They may be limited in how close to your table they can approach, based on where the other tables are, or what the other players are comfortable with, but you can sure bring them. Maybe encourage them to make whatever donation to the EFF they feel comfortable with?
Can I hack stuff at/near the poker room? No. Don’t get me in trouble with the Nevada Gaming Commission. Don’t scare the normies; they get cranky when they have thousands of dollars on the line and the LCDs around them start showing WarGames.
I have more questions! Nifty. Email events@eff.org. Can’t wait to see you there!
November 13, 2023
a process for large meal cooking
I cook at a kitchen for our unhoused neighbors every month, and often am hit with last minute ingredient substitutions, donations of odd ingredients, and interesting food safety questions. Here are some rules for cooking more than 150 meals at once. I assume you’re going to make a large one-pot dish or sauce over a starch; it’s very difficult to assemble and do something more or different than that if you haven’t much experience yet. In addition, there’s very little that can’t be turned into a good tomato-based pasta sauce over a boiled noodle; it’s the best idea if you haven’t done a lot of this before.
Any meat is fine if it isn’t spoiled (smell it, use your senses, etc) because enough garlic, diced tomatoes, and italian seasoning turns anything into pasta sauce. I mean anything. I’ve turned raw bacon cheddar-mixed hamburger patties, ground turkey, cooked pork sausages, flank steak, ground lamb, and plenty of other meats into the base for a sauce.Chop all food small enough that multiple pieces of that food will fit on a spoon. Not only is that best for food safety; it ensures that all foods will cook through and meld flavors in the often-shortened timespan for cooking large group meals.If faced with a large number of prep ingredients, some kind of meat, onions, vegetables, and a starch, and you don’t know what to do first:Start at least one very large pot of lightly salted water boiling; you’ll need that for boiling dry pasta later and it can take 30m for a very large pot of cold water to come to a rolling boil, as well as longer than you expect to come back to a boil after adding more than 10lb of pasta to it.Brown the meat by breaking it apart over a large pan with plenty of oil over very high heat. You don’t have to cook the meat so much that it is food-safe; that will be the liquid boil that will happen in a few steps. You do need to cook the meat past the point that it is browning. You’ll often see meats release a lot of liquid into the pan; the meat will stay gray and pink until the liquid has boiled off. You’ll hear a change in the pan when the meat starts to brown instead of boil; the steam will dramatically reduce and you’ll hear it start to sizzle instead of steam. That’s when to watch and stir carefully to ensure you’ve broken apart all the meats and are starting to get browned at the edges. Treat mushrooms for a vegetarian dish the exact same way you’d treat the meat.Chop whatever onions, garlic, leeks, green onions, and any other aromatics you have. If someone can have been doing this while you were cooking the meat, good. If not, pull the meat off the fire until you can do so, or consider doing this before you start the meat, though it’ll add to the overall time of the cooking and prep.Add them to the meat once it is browned enough that you have started the Maillard reaction. in 5-10m, when the aromatics have begun to turn translucent, you can add whatever vegetables you have prepped. If you have mushrooms, do those first so they can sweat off some of their moisture and get some browning if possible. Mushrooms can contribute to the Maillard reaction.Keeping everything still on high heat, add whatever canned or watery sauce ingredients you have. Often, this is where I’ll add a couple of flats of canned diced tomatoes. Usually I’m adding at least 150% by volume of whatever meats and aromatics I’ve started with…more like 200%. This will turn the meat/aromatic/chopped veg to liquid again, so ensure you’re done browning whatever you had in the pan.Liquid is the best conductor of heat to ensure food safety. If there is a meat dish or anything that must be cooked, it absolutely must come to a solid rolling boil for a minimum of five minutes in enough liquid that the pan doesn’t burn. If you need to add more liquid, add water or chicken broth or vegetable broth. Try to not add a liquid with too much sodium in it; if you started with cured, processed, or cooked meats such as sausages or ham, you may already have added a great deal of several kinds of salts to the dish without yet being able to taste it. If in doubt, use water – you can always add more salt later if needed to get some flavor back, and it’s better than discovering you’ve added way too much salt already.Turn the heat down to medium; this is where you’ll start adding some seasoning and spices. Add your herbs such as Italian seasoning, any kinds of pepper or chile (go easy! this will cook down and the heat will multiply!), and any other flavorings besides those containing sodium. Simmer while you prep everything else.Once the sauce/meat dish has cooled down to medium, taste it a couple of times with plastic spoons or something you can throw away. Don’t double-dip; you’re now below boiling point and to maintain food safety, be cautious about germs. Does it need salt? Always go light on salt because this will cook down further in the time you have before serving the meal. You can always add more later but you can’t take it out. Use a flavored salt when your dish is a bit bland; have garlic salt or chicken bouillon? Use those instead of plain table salt when possible. Turn to medium low and let simmer until you’re ready to start serving. Don’t remove from the heat until you’re guaranteed to have it all served in under 90m and can keep at a safe temperature, such as in a chafing dish.Start the pasta boiling. Make sure to stir a few times. Opt for macaroni, shells, or small pasta rather than longer noodles if possible; long noodles are really hard to not burn yourself with when dumping into a giant colander.Leave that alone and prep a salad dressing. A simple salad dressing for a lot of people is about 12oz of oil and 12oz of vinegar. Whatever you’re cooking, you can follow that simple rule and alter the oil or acid until you have a thematically appropriate dressing. When making a stirfry, I’ve used sesame oil and rice vinegar. When making Italian food, use olive oil and balsamic or red wine vinegar. When making a stew, use avocado oil and lemon juice. Use the appropriate salt – soy sauce works in Asian salads, plain salt for Italian or other side salads. You can add some Italian seasoning to the dressing, as well as fine black pepper and salt. Get a container that can be shaken. You will need to shake the dressing to make an emulsion, and it will separate very quickly, so when you make up big batches of salad, shake the dressing before adding to it. Get big bags of salad greens, and about 6lbs of salad will serve around 50 ppl, with 8oz-10oz of shaken dressing dumped over it. Mix it with your gloved hands; it’s faster. Trust your tastebuds and don’t drown the salad.Have 6-8 long loaves of bread if you don’t know what else to serve as a bread. Cut baguettes on a 60-degree angle to maximize size and surface area by weight while keeping it attractive.When the pasta is done boiling, strain it (don’t worry about all the rules involving not pouring starchy water over noodles; there will be way too much boiling water and weight to worry about that). Put it back in the pot, and put plenty of oil, like cups of olive oil in it to keep it from sticking for the hours it’ll take to serve all of it. Stir it up and keep covered to stay hot and food-safe.Assemble a sample meal. Have one little thing to sprinkle over the top of the meat/pasta dish, because it looks nice and finished that way. Can be parsley or cheese. Parmesan cheese is expensive but if you have the sprinkly kind, that’s fast and easy. If you have a pasta dish, you can do a generous pinch of mozzarella shreds.Get an assembly line going with whoever you have in the kitchen to plate the dishes up as folk come through the line.This process will take you 4 hours with one person (not advised; dumping the pasta pot alone takes two people), 3 hours with two people, 2 hours with three people (the minimum advisable number of people to pull this off), and can’t be done in less than 80m no matter how many people you have in the kitchen. 5-6 people is optimal for this kind of meal prep.Once you’ve done this a couple of times, you can start changing things up and experimenting with different flavors, but this is the most bulletproof process I’ve refined so far. I have no list of ingredients for you but some simple rules are: try to have at least 4oz of pre-cooking protein per person, you can’t go wrong with more starch or more oil on that starch, our unhoused neighbors are often without fresh leafy green food so more is better, and do at least one nice garnish of cheese or herbs.









June 10, 2023
“Yes, but how do I submit a comment on how unintuitive the comment submission process is?”
I’m smashblogging on a Saturday because I came across this story on FedScoop: https://fedscoop.com/white-house-launches-public-consultation-on-critical-ai-issues/ which discusses the Biden Administration’s Office of Science and Technology Policy’s launch of a public request for comment on their upcoming AI policy work. I wanted to Say A Few Words.
The story does not contain a link to the actual request itself.
So unnamed senior government sources that I angrytexted (they also noted the complexity of finding this) found this link here: https://www.federalregister.gov/documents/2023/05/26/2023-11346/request-for-information-national-priorities-for-artificial-intelligence. Oh, says I. So intuitive. So clear to all Americans that obviously some place called Federal Register is where that request for public comment would be. So I check it out, and actually, there’s a link in that document that says I have to go to regulations.gov. I hit that link and guess what: it takes me to regulations.gov. No link to the actual thing I’m looking for. But there’s a search bar. Masochistically, I type in “ai” which, obviously, nets me literally-literally 51,704 results.
I take a stab in the dark; I’m a nerd, and perhaps the document I’m looking for has some form of unique identifier. So I try a search instead by the document number on https://www.regulations.gov/search?filter=2023-11346.
Aha. There it is: https://www.regulations.gov/document/OSTP-TECH-2023-0007-0001
Lo, our journey has ended. I’m annoyed, but this is apparently the site you should go to in order to find any public calls for comment on proposed government regulations. Importantly, I did find the call for comment. It was on display in the bottom of a locked filing cabinet stuck in a disused lavatory with a sign on the door saying ‘Beware of the Leopard’.”
*********
But could I have found it another way? Normal humans might try searching “ai” or “artificial intelligence”; what would their experience be like?
Maybe after searching “ai” the “Only show documents open for comment” checkbox filter will get me somewhere?
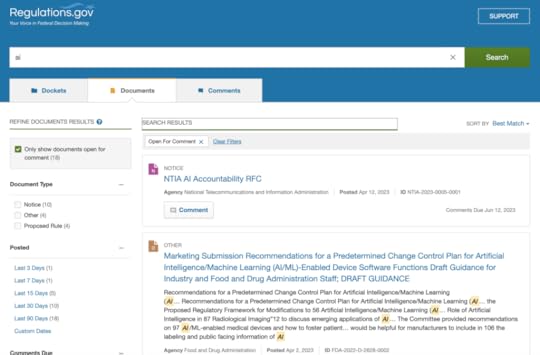
Ooo, the top result looks promising; looks like the NTIA wants some AI accountability. https://www.regulations.gov/document/NTIA-2023-0005-0001. Cool, but that’s not what I’m looking for.
Aha, the third one down is what I’m looking for. Obviously these are not ordered in any human logic, as the top result was from April 12th and the one I want is from May 25th. Fine. I’m steeped in Lovecraftian lore and that gives me an automatic Good Result to my “Find Hidden Item On Government Website” roll.
************
Well, I certainly have some thoughts NOW. *cracks knuckles.*
Again, here’s the link to tell the OSTP and White House what you think of their upcoming AI policy. https://www.regulations.gov/commenton/OSTP-TECH-2023-0007-0001
post script: I wanted to go tell someone how difficult it was to get from any entry point a normal human would have to try to comment on public policy (usually it would be some kind of news story or a link on a social media site) to actually finding the relevant policy. At minimum, when government agencies post an RFC on their sites, it should link directly to the RFC on regulations.gov. I went down a rabbithole and found that to complain to any government agency, you’re supposed to contact their Inspector General office. Turns out that regulations.gov is run by the General Services Administration, and their site is at https://www.gsaig.gov/hotline. Unfortunately, they only seem to investigate claims of misbehavior or fraud regarding government employees. There’s no place I can find to tell them that the UX on regulations.gov could use some love to get to a place where it’s usable for normal humans. But hey, here’s an email address! I’m going to send them this blog post and also a thank you for all they do regardless. There’s (hopefully) a human on the other end of this email, even if they don’t personally have any power to fix the UX, they might know someone who does. Good luck to you! OIG_PublicAffairs@gsaig.gov.
Turns out the real treasure was the new ways to provide detailed and exhaustive technical comments to the Federal government I found along the way.
May 26, 2023
“If you can’t do something smart, do something right.”
Shepherd Book said that in Serenity, a lovely movie from 2005 that wrapped up the sadly-too-soon cancelled series Firefly.
I use it a lot when institutional constraints and incentives stop me from doing the smartest and most effective thing possible. There’s still always room to do something right.
I and Adam Shostack wrote a sturdy schnitzel-und-kartoffelkuchen dinner of an article discussing some of the constraints on the institution called the Cyber Security Review Board. It’s up now at the Council on Foreign Relations here:
https://www.cfr.org/blog/cyber-safety-review-board-should-investigate-major-historical-incidents
We suggest that even though a staggering number of institutional obstacles do lie in the way of the CSRB in terms of acting effectively and immediately, there is a lot of room to do something right—to examine still-reverberating cyber incidents with lessons for us all, and to provide meaningful and nonpartisan history that we can build upon.
I’d suggest reading over your breakfast sometime this weekend. When Adam and I get on this carousel we tend to ride it for a while, and we luxuriated in a lack of word count to let us dig meaningfully into the real issues.
It seems near-impossible for the CSRB under the current circumstances to examine ongoing incidents without fear or favor. We propose there’s a hack to be found here by examining historic incidents with still-relevant technical details. After all,
“Things are only impossible until they’re not.” ~ Captain Jean-Luc Picard
April 18, 2023
What is Montana, anyway?
I talked to a reporter yesterday about the recent TikTok ban legislation passed there, and explained some of the technical difficulties with enforcing any such ban. Hell, even the legislators themselves admit they can’t operationalize and enforce the ban.
So, to clarify what constitutes geography on the Internet, I used some analogies. One of the hardest legal things to do with computers is prove who was using them at the time the computer accessed illegal material. IP addresses are not proof that a *person* did something illegal – they’re only proof that a device either accessed illegal content or that some dastardly criminal forged the return address on the virtual envelope.
What if someone outside the state of Montana signed into their college’s network and downloaded TikTok while not inside the state’s borders…but via the IP block of that college? (I went to college in Montana from 1998-2001, and yeah, that was the Napster heyday). What if someone physically inside the state of Montana downloaded TikTok while signed into a VPN that had exits in an IP block in the state of California?
And the most important question: what if a TikTok download was traced to an IP address at a location inside Montana but there were multiple people who could have had access to it – such as a coffee shop wifi hotspot?
I explained the difficulty of enforcing this ban on any individual person in the state of Montana by saying that this is like automated traffic tickets from cameras. One receives a letter in the mail with a violation date, a URL with photos and videos of the infraction, and a date by which to pay the fine. No one’s insurance is dinged, no moving violation is on anyone’s license – because while the state can prove that a given *vehicle* committed an offense, they can *not* prove who was behind the wheel. They can demonstrate that a given piece of equipment did something illegal, but not who the operator of that equipment had been at the time. The exact same legal issue comes up with proving someone did or didn’t operate a computer at the time of an alleged offense – an issue that comes up quite frequently in Computer Fraud & Abuse Act prosecutions.
Long story short: use analogies to explain stuff to reporters and policy advisors so they can explain it to their readers and principals.



