Per Axbom's Blog
October 10, 2020
Boka tid hos Krys vårdcentral – så ser flödet i appen ut.
Under den senaste veckan har det varit en hel del debatt om Krys fysiska vårdcentraler och hur man som användare av deras app styrs mot att lista sig hos vårdcentralen när man ska besöka den, även om det rent formellt inte behövs.
I Stockholm grundar sig ersättningen till vårdcentralerna till 60 procent på hur många patienter som är listade vid respektive vårdcentral, samt till 40 procent på hur många besök som faktiskt blivit gjorda. Sedan 2017 finns också en ersättningsmodell som innebär att man får mer ersättning för vård som kräver mer resurser, som exempelvis vissa kroniska sjukdomar. Att ha många listade patienter är i stort väldigt lönsamt, och blir man av med listade patienter kan det få stora konsekvenser för en vårdcentral.
Kritiken handlar om att många patienter säger sig ha listat sig på Krys vårdcentraler av misstag. En del människor, oklart hur många, har inte förstått att begreppet “lista sig” innebär att man listar sig som patient på ett sätt som man bara får göra en gång. En patient i Stockholm får bara ha ett vårdval. Därför har flertalet patienter klagat och valt att gå tillbaka och lista sig hos sin tidigare vårdcentral.
Exakt hur omfattande problemet är och hur flödet faktiskt ser ut har dock inte framgått. Jag tänkte att jag kan bidra med lite kunskap om det senare. I filmen nedan har jag spelat in flödet som det ser ut i Krys app.
Observera att det jag primärt vill visa här är hur informationen om listning ser ut i flödet. Man kan sannolikt starta flödet för omlistning på flera olika sätt, och enligt rapporter dyker erbjudandet om listning alltså upp även när man bokar digitalt möte med en läkare eller ska förnya recept.
Förutom att media gör stora antaganden baserat på otillräcklig information (hur många är egentligen drabbade av missförståndet?) så tycker jag det är synd att så få visar läsarna det exakta flödet som är i fokus, när det är så lätt att göra det.
Jag tycker också att Krys svar lämnar en hel del att önska. Så här kunde Kry ha svarat på kritiken:
“Vi värnar om att människor ska må bra. Om det är så att människor blir förvirrade av hur vi skriver eller visar information, och det visar sig att det inte är med avsikt som de listar sig på vår vårdcentral, så behöver vi förstås ändra eller komplettera hur vi presenterar den informationen.”
Deras svar är i stället olika varianter av: “Vi följer lagen.”
Det är alltid värt att påminna om är att etik och lag förstås inte är samma sak. Även det som är lagligt kan ha negativ påverkan på människor.
Det jag som medborgare och humanist efterfrågar är ett tydligare fokus på människans autonomi, välmående och förmåga till välinformerade beslut. Dit når vi genom relevant och begriplig information, såväl från media som från företag. När dessa parter misslyckas med att stärka medborgarnas förmåga till informerat samtycke så måste förstås ändringar i offentliga regelverk, och lagstiftning, träda in.
Det är alldeles för lätt att glömma att människor som använder dessa appar ofta befinner sig i ett sjukdomstillstånd (det är till och med hela poängen), att apparna är till för ALLA medborgare, och att vi därför bör ställa höga krav på deras förmåga att ta hänsyn till variationer i kognitiv förmåga vid användning.
Vi vet fortfarande inte hur stort problemet är. Vi kan absolut göra antaganden baserat på stora tillströmningar av listade patienter. Men vi vet inte. Det är för mig det mest frustrerande i den här historien.
Nu skärper Stockholm reglerna
Debatten om primärvårdens ersättningssystem är förstås alltid värd att följa.
Kry får 50 procent mer i ersättning av Region Stockholm för alla digitala besök i regionen. (SvD betalvägg)
”Inför ett nationellt ersättningssystem i primärvården”
Ersättningsmodeller för vårdcentraler kan förbättras: ACG-systemet medför överdriven diagnosregistrering som kan göra patienter sjukare
September 23, 2020
Why I avoid using Zoom for meetings
Zoom is a nine-year old company with growing pains. When I mention that I don’t use Zoom people tend to respond: “well they’ve fixed all their problems now”. Yes, they started fixing some of the problems they had for nine years after the flood of criticism started… not in any way proactively. I just want to do a run-through of why I avoid Zoom that goes further than a few “glitches”. To stop using it completely is not possible with a tool as prevalent as this, but there are ways to use Zoom more carefully – I’ll advise at the end of this post and list alternatives.
July 11, 2019: Apple has pushed a silent Mac update to remove hidden Zoom web server
In July of last year we learned that Zoom was installing a hidden web server on mac computers. Because of it, any website could forcibly join a user to a Zoom call, with their video camera activated, without the user’s permission. The vulnerabillity was discovered by Jonathan Leitschuh and disclosed in his Medium article: Zoom Zero Day: 4+ Million Webcams & maybe an RCE? Just get them to visit your website!
July 24, 2019: Opinion: Zoom’s handling of vulnerability disclosure highlights the dark side of bug bounty NDAs
“Zoom’s handling of a cybersecurity researcher’s responsible disclosure of several serious vulnerabilities in its video-conferencing application is baffling. In March, cybersecurity researcher Jonathan Leitschuh contacted Zoom to notify the company of three major security vulnerabilities existing within its video-conferencing application for Mac computers.”
a bug that allowed a malicious attacker to launch a denial of service (DOS) attack on a user’s machine,
a bug that left a local web server installed on the user’s Mac even after uninstalling the Zoom application,
and also a gravely alarming vulnerability that allowed for a malicious third-party entity to remotely and automatically enable an unsuspecting Mac user’s microphone and camera.
As outlined in Leitschuh’s blog post, he gave them the standard 90 days to fix before going public.
“In its initial response to the public disclosure on the company blog, Zoom refused to acknowledge the severity of the video vulnerability and ‘ultimately…decided not to change the application functionality.’ Although (only after receiving significant public backlash following the disclosure) Zoom did agree to completely remove the local web server that made the exploit possible”
Zoom had little interest in fixing these issues and tried to really downplay their severity.
January 20, 2020: Zoom vulnerability would have allowed hackers to eavesdrop on calls
Cybersecurity research company Check Point Research found security flaws in videoconferencing platform Zoom that would have allowed a potential hacker to join a video meeting uninvited and listen in, potentially accessing any files or information shared during the meeting. A Zoom spokesperson said the issue Check Point identified was addressed in August of 2019.
March 19, 2020: Advocacy group calls for Zoom to release a transparency report
“Publishing transparency reports is a common practice for larger tech companies. Google and Microsoft, for example, share the number of requests they get from law enforcement and from governments for user data and if they disclosed customer data as part of those requests.” Access Now published an open letter urging Zoom, given its impact and position on the global stage, do the same.
Given Zoom’s increasing role and user base, it is imperative that you issue a regular transparency report. According to your website, you are the “leader in modern enterprise video communications,” and Bernstein Research analysts reported that Zoom has gained more users so far this year than in all of 2019. This trend is likely to continue as more people rely on video conferencing services to carry on in their work and lives.
Zoom promised to publish a transparency report on June 30, but has failed to so: Zoom misses its own deadline to publish its first transparency report. They now say it will be out later this year, but have given no date.
“Though it is commendable that Zoom has taken steps over the last 90 days to update some of its security and privacy practices, the decision to delay the transparency report signals that Zoom does not prioritize reporting,” said Isedua Oribhabor, a US policy analyst for Access Now, in a statement to The Verge. “The pressure that Zoom has faced from the Chinese government to restrict accounts underscores just why a transparency report is essential — without it, users have no insight into the extent of government interference with their accounts and data or the steps Zoom takes to push back.”
March 25, 2020: Zoom Can Track Who’s Not Paying Attention In Your Video Call. Here’s How.
We are made aware of Zoom’s attendee attention tracking feature. As Zoom describes it: “Hosts can see an indicator in the participant panel of a meeting or webinar if an attendee does not have Zoom Desktop Client or Mobile App in focus for more than 30 seconds while someone is sharing a screen. ‘In focus’ means the user has the Zoom meeting view open and active.” Users can disable the tracking feature in their account settings, but the administrator can also make this setting mandatory for all users by clicking on the lock icon.
This type of automated quantitative analysis claiming to give an indication of something it really doesn’t can be extremely misleading. As a person who myself has other windows open while listening (sometimes for drawing a mindmap, sometimes for finding links and research, and for other reasons that are not anyone’s business) I know how terribly wrong these indicators can be, and the worry is of course that people in power draw the wrong conclusions and people unable to defend themselves (students and more) suffer from it.
EFF has some added words of caution:
If a user records any calls via Zoom, administrators can access the contents of that recorded call, including video, audio, transcript, and chat files, as well as access to sharing, analytics, and cloud management privileges.
For any meeting that has occurred or is in-process, Zoom allows administrators to see the operating system, IP address, location data, and device information of each participant. This device information includes the type of machine (PC/Mac/Linux/mobile/etc), specs on the make/model of your peripheral audiovisual devices like cameras or speakers, and names for those devices (for example, the user-configurable names given to AirPods). Administrators also have the ability to join any call at any time on their organization’s instance of Zoom, without in-the-moment consent or warning for the attendees of the call.
March 26, 2020: Zoom iOS App Sends Data to Facebook Even if You Don’t Have a Facebook Account
Certainly not the only app that does it, it’s almost common practice. But nothing in Zoom’s privacy policy addressed it (not that this would’ve have made more people aware). Zoom pledged to remove the Facebook SDK (Software Developer Kit) to remove this data sharing. But again, this is done after others pointing it out to Zoom, not something that Zoom themselves tended to proactively. How many years has Zoom been in business again?
March 30, 2020: FBI Warns of Teleconferencing and Online Classroom Hijacking During COVID-19 Pandemic
During the corona outbreak and the explosive increase in usage of Zoom, even FBI had to issue a press release warning about Zoombombing:
As individuals continue the transition to online lessons and meetings, the FBI recommends exercising due diligence and caution in your cybersecurity efforts.
March 30, 2020: Zoom Tightens Privacy Policy, Says No User Videos Are Analyzed for Ads
“Zoom’s privacy policy allowed the company to collect information from users’ meetings—from videos to transcripts to the notes you might have shared through Zoom’s chat feature. The privacy policy didn’t prevent Zoom from using that personal information for targeting ads on or off the platform, or for other business purposes.” They’ve now changed that.
From the same article:
In addition, Zoom told Consumer Reports that it would stop retweeting Zoom screen captures posted by teachers that included images of students. (If you’re a teacher, don’t do that.)
March 31, 2020: Zoom meetings aren’t end-to-end encrypted, despite misleading marketing
Why Zoom would claim end-to-end encryption is beyond me. It’s very difficult to achieve on a video conferencing platform and for a company that has been in the video conferencing business for nine years, and whose CEO worked at developing Webex, it’s either a testament to gross negligence or intentionally misleading to state this. Anyway, they don’t claim this anymore now. After, yet again, someone on the outside pointed it out.
April 1, 2020: Zoom is Leaking Peoples’ Email Addresses and Photos to Strangers
Honestly, isn’t this a rookie mistake? If people are on the same domain Zoom assumes you are entitled to all their personal details. They blocked this for the common personal domains like Hotmail and Gmail, but there are obviously thousands upon thousands of other email providers out there.
Typical tweet:
“I just had a look at the free for private use version of Zoom and registered with my private email. I now got 1000 names, email addresses and even pictures of people in the company Directory. Is this intentional?,”
But wait for it, it gets better: The way Zoom manages this to protect people is by self-reporting(!) and adding domains to a blacklist.
“Zoom maintains a blacklist of domains and regularly proactively identifies domains to be added,” a Zoom spokesperson told Motherboard. “With regards to the specific domains that you highlighted in your note, those are now blacklisted.” They also pointed to a section of the Zoom website where users can request other domains to be removed from the Company Directory feature.
So it’s opt-out (by a reporting process) rather than opt-in. Thanks for that Zoom.
April 4, 2020: Zoom admits some calls were routed through China by mistake
Growing so fast, Zoom forgot to check what datacenters are used to balance the load. But, it’s not like Zoom is in the habit of making mistakes that endanger people’s privacy…
Even more interesting from the same article is the reference to encryption, as pointed out by Citizen Lab:
But some questions remain. [Zoom] only briefly addresses its encryption design. Citizen Lab criticized the company for “rolling its own” encryption — otherwise known as building its own encryption scheme. Experts have long rejected efforts by companies to build their own encryption, because it doesn’t undergo the same scrutiny and peer review as the decades-old encryption standards we all use today.
Zoom certainly does seem like a company on top of things and working proactively with risk mitigation… 
September 4, 2020
#UXCopenhagen talk: First Design No Harm (video)
My talk from UX Copenhagen earlier this year is now online. It’s an emotional talk that takes its start in a story of abuse and the systems that support that abuse. As designers we have the power to abuse, but how aware are we of when this happens?
Find the transcript of my talk below the video. You can also access my conference slides and my first blog post on this topic.
Transcript of the talk First, Design No Harm
This year it’s exactly 30 years ago since I started high school in Sweden, at a boarding school where I lived in a dorm with 25 other boys aged 14-19. Only one month into this experience I found myself standing in line for breakfast in the dining room, and there was a lot of commotion and nervous laughing going on.
The reason for this was that during the night four of the last-year students had barged into the rooms of three first-year students, pinned them down on their beds, stripped off their underwear and shaved off their pubic hair.
This had been a spontaneous hazing ritual wherein young students are welcomed into the brotherhood of the dorm. While this was perhaps one of the more severe happenings, these rituals were not uncommon and often involved physical harassment and embarrassment of a sexual nature.
Upon leaving the school it took me several years to stop defending these practices and recognise how wrong they are. And it was only a few years ago I last saw parents on TV, mothers, still defending how these behaviours are part of the activities that build character and friendship.
After many years of reflection I have boiled down my own and others’ unwillingness to admit how vile the activities in fact are, to this simple truth:
If I admit that it was a situation of abuse then I would be forced to myself reconcile with the idea of being a bad person.
Unsurprisingly, most of us resist doing this.
Sometimes I would tell myself that at least I did not physically harm people, but when I’ve revisited my own behaviour I was able to see how this was not about individual events, but about a systemic behaviour that I of course played a part in.
I was a child. But I assumed the environment I was in to be my identity. I assumed the people in my vicinity to be my community. And I adopted the rules and mindset of this community.
I did intervene in the beginning. I was one of several people who leaked to the press what had happened. After media attention, the four perpetrators were expelled one month before their graduation.
You might think of this as justice served but that is only if you fail to consider how those three young men had themselves been abused, at the same school, since the age of 14.
As more and more people find themselves defending unethical practices in design I hear CEO’s, managers, design leaders and people in behavioural economics profess some variant of this statement:
If you screw people over they are going to stop doing business with you, and they’ll tell all their friends to stop doing business with you.
Essentially, if you abuse people, they will leave. And, if they have friends, they will tell all of them. I believe it’s fair to say that these privileged people are speaking of how they would expect themselves to behave.
Let me share five reasons research shows why people often DO NOT leave abusive relationships. There are certainly more.
1. Society normalises unhealthy behaviour so people may not understand that their relationship is abusive.*
“Everyone collects data and exploits it for their own benefit.
Everyone learns about habit-forming techniques to attempt to influence people one way or another.
Everyone hides important information in the privacy policy.
Everyone ties me up in long-time subscriptions.
How could it possibly be bad – surely this is how business is done and I have to just learn to live with it.”
2. Victims feel personally responsible for the abusive behavior.
Self-blame is strong in all of us.
“I bought the wrong thing, but that’s probably just me.”, “I signed up for that trial period but it’s my fault I’m now stuck in a 12-month contract.”, “I can’t seem to stop checking notifications but that’s only my own lack of self-control.” “Theyused my Instagram photo about being raped but it’s my fault for not reading the terms of service.” “Wow I’m so bad at computers I’m sure everyone must be laughing at me behind my back.”
It is obviously never your own fault when you feel betrayed and are taken advantage of. But other people in our life seem to be coping so we often assume it must be.
3. If you stick it out, things might change.
You’ve had good times together, there is a possibility that things could get a lot better. There certainly are things you would miss. And now that the media is writing about ethics maybe these platforms will get it and start treating you better. I’m not sure how that will play with their business model, but you know, it can really only get better, can’t it?
4. You share a life together.
As part of many teachings around behavior and design, it is recommended that one lets the users invest time, effort and emotion in a service by having them for example upload pictures, change colors and profile pictures. Of course, the more a person invests in this “life together”, the less likely it is that they will want to abandon it, even when you treat them poorly.
5. Leaving is made difficult
I’m confident there are many of us who have experienced the ease with which we sign up for services, as well as the obstacles erected to prevent us from leaving.
Once we adopt a mindset where we allow profit to come at the expense of human well-being we are enforcing an abusive relationship.
If you as an employee want to do something to avoid causing harm to someone else, but your manager does not permit you, that is an abusive relationship. And to build on that, if you use design to coerce people to do things that are not in their best interest, that is an abusive relationship.
And should things fall apart, now you can blame your manager and your manager can blame his profit-based performance indicators.
When I finally acknowledged how the digital design industry was moving in the direction of conversion optimisation at any cost, and unethical behavioural nudging for profit maximisation, I was concerned many of us had completely lost touch with why we became designers.
Every student, coaching client and colleague I talk with share the same core.
“I want to help people.”
What also happens when you put yourself in a position to help people of course, is that you gain the ability to misuse that power, the ability to abuse. We need to recognise and talk about this power. Constantly.
Because if we don’t give it a voice, the abuse becomes invisible.
As it happens, having the power to help, and to influence others, is a slippery slope. You make compromises, You take one step in the wrong direction – a little nudge, a shove and sprinkle of dark patterns, some neglect of vulnerable people. Now the next step doesn’t seem that bad. And your actions did, after all, turn out to be profitable. You got a pat on the back from the people close to you. And the users, way across somewhere else, did after all choose to click all on their own.
Pretty soon you are the person saying…
Well hey, if they don’t like it, they can just leave.
Seeing the harm becomes ever more difficult as the harm itself just becomes part of a systemic habit loop and normalised. That’s why it becomes so important to make the harm visible, to create awareness.
A lot of harm is of course becoming visible today as we talk more about tech addiction, mass surveillance and data exploitation. Less visible is the part we, as designers, are playing in a race that can both empower and dehumanise at the same time.
A person recognised across the world as a a prominent design leader was last year asked on stage at a big industry event how the Hippocratic Oath should be applied within the field of design. The Hippocratic Oath, of course, is an oath of ethics historically taken by physicians and one of the most known Greek medical texts, of which a primary tenet has become: “First, do no harm.”
In a disturbing response, this design leader argued that doing no harm as designers would imply that we never do anything new and never take risks. Instead he argued that “We need systems in place to ensure that we don’t do too much harm. Or we don’t harm intentionally.”
Let me repeat those words:
“Don’t do too much harm…”
It is extremely dangerous when design leaders suggest that an ethical code would somehow be detrimental to the design outcome. Many designers are out there are listening, essentially hearing that risk-taking takes precedence over avoiding harm. That some abuse will be “worth it”.
Let me be abundantly clear.
Ethical codes support risk-taking, that is what saves lives.
Ethical codes support innovation and making new things. This is how medicine and life-supporting devices are made.
Ethical codes support moving forward, just always aligned with the mindset of minimising harm.
That is why the ethical codes matter.
I will be honest, medical ethics, like any ethics, is not black and white. And medical history certainly has it’s share of disturbing abuse of human beings in the name of science.
But the availability of codes such as the Hippocratic Oath, The Declaration of Helsinki and The Nuremberg Code allows us to keep the conversation going. Because the codes themselves are not the final product but rather the topics that always need to be within our conversations to help us stay away from becoming the abusers.
As designers our curiosity should be driving us to explore the extensive and thoughtful work that has gone into reasonings around avoiding harm to humans. We should be reading all of it, because then we can begin to understand why something that may sound counter-intuitive is expressed out of care for human well-being.
Here are 6 things medical ethics can teach us:
1. It is not recommended to always treat patients as you yourself would like to be treated.
I’ve seen many designs that work well and efficiently for tech-savvy people. But not for the rest of the population. In Sweden, I know people who find it extremely difficult to pay for parking or public transport. Things that only a few years ago were second-nature to them. We treat people differently because we are all different, with different experiences, preconceptions and abilities.
2. Risk-taking to improve well-being is fine, but only with the full, informed consent of the person at risk.
This is the simple difference isn’t it? Instead of just taking my data, tell me what you are taking and why, how you will use it and how you will not use it. And what measures you are taking to protect it. In medicine there are ethical review boards that include people from different specialties and backgrounds. When in any doubt, ask help from a diverse review board to understand all the risks, and explain the risks to the people at risk.
3. People have a right to make decisions that are bad for themselves.
In a world of covert nudging where designers are working to influence people to do what they or their company has decided is best, we are working against the care you must take to allow for people to make different choices than the ones you believe are the right ones. Appreciate the importance of autonomy and give people the option of not following your lead.
4. Be open about lack of knowledge.
If you don’t know you don’t know. As designers we work with experiments and hypotheses. Expressing views with 100% certainty on “This is what users need”, “This is how they behave.” or “This is what they feel about the outcome” is irresponsible. Be open about your lack of knowledge to support necessary conversations about how we listen for mistakes in our assumptions.
5. Avoiding harm is not enough, you also have to take steps to contribute to well-being.
This is the difference between standing still and moving forward. If you’re not contributing to well-being, you may have to remind yourself why you become a designer.
6. Think about, discuss and record ethical considerations and feel confident that you can justify your decisions.
In the end ethical design is a process, not a set of rules.
And by documenting your design decisions and your concerns along the way, you will feel immensely more confident and happy about the work you’re performing. We all make mistakes. Document them. Regularly. Do better next time. And make others aware.
Remember, it’s not the code of ethics that helps patients, it is medical personnel with a strong sense of understanding that they can potentially harm people.
It is not a code of ethics that helps users of digital services, it is design professionals with a strong sense of understanding that they can potentially harm people.
The code is there to support an ongoing conversation that contributes to that awareness.
Whereas medical workers often are close enough to touch and look into the eyes of their patients, in the digital space we are often many degrees away from the people we are influencing. In time, in space and even in the potential number of actors between our design and what the experience becomes.
This does not remove accountability, but instead adds a layer of responsibility. We, as designers, are the ones who can bridge that distance and help people in the now, become better aware of the people they are affecting in the later.
When I sit with developers and talk about the importance of accessibility I do not talk about technology. I do not delve into the many criteria of the Web Content Accessibility Guidelines. I do not show them tools for validating their pages.
I talk about people.
I talk about Jenny who has a visual impairment and is trying to order a guitar. I talk about James trying to fill in a job application while his 2-year old is making a fuss in his lap. And I talk about Jasmine who struggles with her reading comprehension and has difficulties with metaphors.
I want to help developers understand why they are building for accessibility. If they understand why they will figure out the how. By being a designer who can trigger compassion, I build motivation to do the right thing. Equally important, I’m treating members of my team as human beings, not resources.
As a designer I can bridge the gap between the person who builds and the people being affected.
They may not be looking into each others eyes, or feeling each others presence. I may not always be able to get them to meet. But I want them to get as close as possible.
To support that conversation and awareness.
Last week I watched a news story on the ongoing pandemic in which a nurse explained how she walked into work every day with a smile and full of intent to help people. What she said had an impact on me: “The virus helped me remember why I chose this profession.”
I encourage you to work in ways that help you remember why you chose your profession.
August 5, 2020
Embed YouTube videos without cookies
Many companies, media outlets and bloggers enjoy sharing YouTube videos on their sites. The problem is that YouTube sets a tracking cookie (for marketing purposes) by default. This poses all kinds of problems when it comes to GDPR – because generally people have not consented to this tracker when they visit a website that is not YouTube itself. But there is also a YouTube setting that seemingly allows you to avoid this cookie.
Let’s say I want to share this video with Shoshana Zuboff talking about surveillance capitalism on Channel 4.
When I click “Share” and then “Embed”, YouTube provides me with en embed code. It’s easy enough to copy this code and be done with it. What many still have not discovered is that if you scroll down, there is an option to “Enable privacy-enhanced mode”. This changes the embed code and that’s the code you should be using, at least in theory. Note: this will send a message of your intent, but it won’t stop people from being tracked.
Here’s a video of how this is done on the YouTube website:
If you’re alert, you may notice that the only thing that changed is actually the URL-embed. That URL changed from
https://www.youtube.com/embed/QL4bz3QXWEo
to
https://www.youtube-nocookie.com/embed/QL4bz3QXWEo
It turns out that YouTube’s official URL for embedding videos that do not set a HTML cookie immediately is youtube-nocookie.com. What this means is that if you are not using YouTube’s own embed code for YouTube videos, then you can just change the primary domain of all domain URLs.
Here’s how YouTube describes Privacy-Enhanced Mode:
Privacy-enhanced mode allows you to embed YouTube videos without using cookies that track viewing behaviour. This means that no activity is collected to personalise the viewing experience. Instead, video recommendations are contextual and related to the current video. Videos playing in privacy-enhanced mode won’t influence the viewer’s browsing experience on YouTube.
Here is where it gets tricky, because this talks about “viewing experience” and says nothing about using the information to build on the User Profile – the data about that Google uses to deliver personalised ads, at the core of Google’s business model. Embedding YouTube videos and staying within the law is a more difficult endeavour than you might imagine.
How YouTube is disregarding your intent (and GDPR)
I was alerted on Twitter by Joey Kant about how gravely misleading the nocookie “privacy-enhanced” setting is on YouTube. As it turns out this is what is happening as you try to embed YouTube videos without cookies:
If you use the youtube-nocookie.com domain, there is no cookie set when the page with the YouTube embed loads.
Instead, YouTube utilizes something called Local Storage in your browser to store a unique device identifier. Note that this is done without anyone’s consent and GDPR is violated already in this step. GDPR is not only about cookies.
As soon as a user presses Play on the video, a cookie from YouTube is set. Whether or not consent has been given from the viewer. The second violation of GDPR in the same embed.
This is how a report from CookieBot describes what is going on:
“Privacy-Enhanced Mode” currently stores an identifier named “yt-remote-device-id” in the web browser’s “Local Storage”. This allows tracking to continue regardless of whether users click, watch, or in any other way interact with a video – contrary to Google’s claims. Rather than disabling tracking, “privacyenhanced mode” seems to cover it up.
So in giving the appearance of caring for user privacy, the act of using “Privacy-enhanced mode” is actually exacerbating the tracking problem.
This is how W3Schools describes Local Storage:
The localStorage and sessionStorage properties allow to save key/value pairs in a web browser.
The localStorage object stores data with no expiration date. The data will not be deleted when the browser is closed, and will be available the next day, week, or year.
Here is the screendump from Local Storage that Joey Kant shared. Note how it is tied to the “youtube-nocookie.com” domain.
And if you want more to worry about, Samy Kamkar – once famous for the 2005 MySpace worm – has created a demo called EverCookie which shows how to exploit at least 10 storage spaces on a computer (including Local Storage) to store information on a user even when they have cookies turned off.
How can I embed YouTube videos legally?
First, have a think about if you need to embed YouTube videos, or if having a picture of them and linking to the website works as well. To be fair, this doesn’t really protect users, or make them more informed, it just pushes it away from being your problem to manage.
For a video embed to go down properly, this is what would have to happen:
The page with the video loads, but the embed is blocked from the start (for the tech-savvy: it can not be part of the DOM on page load)
In place of where the video should appear, you need a message that explains to the visitor what happens should they want to play the video.
When the user clicks, the consent is logged and the video embed is loaded (for the first time).
Now formally, you would only have to ask this once and have it apply for all YouTube embeds on your website. I would prefer it to ask every time, to make users more conscious of the practice, but certainly I would not assume consent for YouTube marketing cookies to last more than a few weeks for a website. Ask again.
Here’s an example on en EU site, The European Data Protection Supervisor, where you can see how this would work. I’ve initiated the process of implementing it on all my sites as well. Here’s an image of that consent window, which is blocking a YouTube video:
 Screendump of a consent window forced upon a YouTube embed, indicating that the content is hosted by a third party.
Screendump of a consent window forced upon a YouTube embed, indicating that the content is hosted by a third party.To make this type of consent happen, you may have some people on your staff with the competence to build it, or you can use a third-party service such as CookieBot to implement and manage consent on a site-wide basis. It’s a compulsory investment either way if you can’t avoid YouTube embeds.
My call to action
Sit down with your team and have a discussion about how you’re going to manage YouTube embeds, both going forward and all the embeds you already have. Bring in providers of content management systems, and tech advisors as needed. It’s almost certain that you are breaking the law today, by not asking consent for YouTube’s trackers.
Make some noise. How YouTube is in violation of GDPR and still making it immensely difficult for website owners to comply with GDPR as well, is a thing to be questioned and investigated.
Thank you for caring about privacy on behalf of your visitors. 
P.S. If you yourself are hosting corporate videos I would generally recommend using Vimeo or Wistia. You’d still need consent for these sites though, but for statistics rather than marketing.
Also, if you want to watch that video Shoshana Zuboff, it’s right here. It uses the youtube-nocookie domain, but if you press play, YouTube will still set a marketing cookie. I am now blocking the content using Borlabs Cookie plugin for WordPress. This means that this block, requiring consent, is applied across all of my websites in an instant.
Trump debates Trump by Justin T Brown
Yet another video is about to make the rounds without crediting the original creator. The maker in this case is Justin T Brown, who has made an edit of the Axios interview with Trump, to make it appear as if Trump is interviewing – or debating – himself. The result is hilarious:
Hundreds upon thousands of accounts will likely download this video from different locations and share it either as their own content or pretend to not know where they found it. If they uploaded it to their own account, you have to ask “Well, where did you get it in the first place?” Why isn’t even that source credited? There is always a source.
I was alerted to this video by my partner in crime James Royal-Lawson and when I raised the issue of the lack of creator credit we went on a quick detective hunt. It didn’t take more than minutes as others had done the work before us. Cody Johnston had already found the YouTube channel, but even then we couldn’t be sure. A YouTube channel with only 7 followers (it has more now) and two videos: one making fun of Biden and the other making fun of Trump. There were still doubts as to the authenticity of this as the source.
I did a search for “Justin T Brown” on Twitter and noticed that most mentions of that name were crediting him as the creator of this video. This is how I found that Austin Tolin had done his due diligence and located Justin’s Instagram account.
And the latest post on this instagram account was of course the video. A further step allowed us to feel even more confident in Justin’s competence. A click on his profile link brings us to his website: justinbrownpost.com. As it turn out, Justin Brown actually appears to work with video production.
If you don’t know who made it, share where you found it
Please do not share content without crediting creators. If you have to(?) share without knowing, at least disclose where you got the content! in this case it was The Lincoln Project who started sharing the video without credit but instead asking the innocent(?) question “Who made this?” That’s not good enough. The immediate question back should be “Where did you get it?” Also, finding sources usually takes less than five minutes using a search engine on one or several social media platforms.
People make stuff, sometimes it gets popular and sometimes not. But freeriding on other people’s content without even a nod in their direction is not a good look. We can probably all do better.
An hour ago Justin himself added this comment to his YouTube video:
Ummm… I just realized this kind of popped-off. Unexpected, but appreciated – thank you. More importantly -> fuck this guy, Black Lives Matter, COVID is the appetizer to Climate Change, get involved in your communities, grow a garden, justice is what love looks like in public, and solidarity forever.
July 12, 2020
Digital Ethics – The Mindmap
This mindmap is a work in progress. It helps me create the syllabus for my course Ethics in Design, as well as outline corporate workshops. It helps to draw from when I’m preparing talks and lectures. It reminds me of the complexity of the system, but also of why it matters to work intentionally with Digital Ethics today.
Maybe it can be of help to you as well.

I’m aware the mindmap isn’t accessible for everyone in its image format. The hierarchical structure of the mindmap is available in this PDF.
July 4, 2020
Vem vet till slut hur maskinen funkar?
Snabb skiss kring komplexiteten i vad vi söker i sociala medier, vad vi får, och vad som driver företagen bakom. Till slut vet ingen hur trådarna däremellan egentligen hänger ihop.
Inspirerad av Ralph Hammers inlägg, Make me Think! och Jordan Lejuwaans Amusing Ourselves to Death: Huxley vs Orwell.

Återanvänd gärna efter behag, och ge gärna kredd med länk tillbaka hit. 
July 1, 2020
The slavery supported by that device in your pocket
When I look at my phone I think about slavery. I think about modern day slavery, perpetuated by the wealth and power that historic slavery facilitated. I think about how invisible it is despite modern day access to information and education. And despite all the many examples of injustice exposed thanks to tech. Here’s the thing: Slaves don’t have access to a school system that can teach or empower them to speak up. Slaves don’t own smartphones. Slaves are just one part of how smartphones come to exist.
» This is the prelude to an article I recently wrote for Ethical.Net. Keep reading in the Ethical magazine
June 29, 2020
Hur arbeta tillgängligt när teknik och digitalisering utvecklas fortare än lagen?
Tidigare i vår hade jag äran att få inledningstala i ett av temaspåren på konferensen Digin, en nätverksdag om digital inkludering och tillgänglighet.
På temat “Hur arbeta tillgängligt när teknik och digitalisering utvecklas fortare än lagen” resonerade jag om utmaningar, fallgropar och risker. Och förstås möjligheter. Eller som Terese Raymond uttryckte det, “Du ryter ifrån så elegant i den här videon.” Oerhört tacksam för den recensionen.
Du hittar hela texten (talmanuset) till mitt brandtal nedanför videon.
Talmanus
Hej, jag heter Per Axbom
Det här är en film med en introduktion till ett temaspår på nätverksdagen Digin. Jag delar med mig av MINA inspel och erfarenheter.
Sedan är det upp till er att diskutera vidare ERA tankar, frågor, utmaningar och lösningar.
Ämnet för det här temaspåret är ” Hur arbeta tillgängligt när teknik och digitalisering utvecklas fortare än lagen?”
Det handlar om hur vi får med tillgänglighetsperspektivet när den digitala utvecklingen ändrar förutsättningar, beteenden och behov, till exempel med AI och robotisering.
Jag har själv arbetat med digital tillgänglighet i cirka 20 år och både konsultar och undervisar inom digital etik.
————————
Jag brukar fråga människor om de vet när Sverige fick allmän rösträtt.
Svaren kan variera, men främst för att man är oense runt om det var när beslutet om kvinnlig rösträtt godkändes i riksdagen, 1919, eller när kvinnor faktiskt röstade första gången, 1921.
Väldigt få svarar 1945. Det var först då som människor som bodde i fattigstugor fick rösta. Ännu färre svarar 1989. Först då slutade vi omyndigförklara många människor med funktionsnedsättningar. Det var alltså först 1989 som vi i Sverige slutade ta ifrån svenska medborgare deras rösträtt, trettioen år sedan.
Hur vi tolkar begreppet allmän rösträtt avgörs av den utbildning vi får, vår egen nyfikenhet och förstås även av samhällets och våra egna värderingar.
Det vi vet med säkerhet är att värderingar förändras över tid.
Spola fram till 2020 och den digitala tekniken har gått ifrån att lova oss en revolution inom demokratisering och inkludering till att uppmärksammas som ännu ett verktyg med potential för att skapa enorma klyftor i samhället.
Jag möter människor idag som har svårt att söka jobb, har svårt att betala för parkering eller bävar för att köpa biljett till lokaltrafiken. Det är inte för att de aldrig kunnat göra detta. Tvärtom, för tio år sedan hade de inga problem med alla dessa aktiviteter. Men… i digitaliseringens namn förändrades landskapet helt, utan något särskilt erbjudande och stöd för att klara övergången.
Det är inte alltid så enkelt att teknikutvecklingen sker snabbare än lagstiftarna hinner med. Bristande tillgänglighet räknas redan som diskriminering i våra lagar. Men vi saknar lagar som handlar om principen för snabb förändring. Regelverk och riktlinjer som adresserar snabba byten av utrustning för samhällets centrala aktiviteter och rutiner.
Vi saknar beslutsfattare som ser riskerna.
Många är duktiga på att se möjligheter och lyfta de problem vi LÖSER med digitalisering, robotisering och AI. Men är avsevärt sämre på att identifiera, vara öppna med och prata om de problem vi skapar. Självkörande robot-leveranser låter fantastiskt för den som är bunden vid sitt hem, men om samma robotar fastnar och blockerar vägen för rullstolar så skapas nya problem.
Det pratas idag om hur självkörande bilar ska kunna ta ett beslut om vem som ska dö när ett barn, en hund och en en person i rullstol plötsligt befinner sig på vägbanan. Det pratas alltför lite om hur vi ska skapa en situation där en programkod aldrig tar beslut om människoliv.
Det är också fel att tro att bara självkörande bilar dödar.
Många människor med funktionsnedsättningar befinner sig i en oerhört utsatt situation där det är svårt att få jobb, man möts av fördomar och i värsta fall trakasserier och våld. I Sverige har studier visat att risken för självmord är betydligt högre hos unga vuxna med aktivitetsersättning än hos andra unga i samma ålder.
Samtidigt kan många webbtjänster använda sig av ångestframkallande språk och interaktioner. En del tjänster ropar “Tio människor tittar på det här hotellrummet just nu!” eller skickar notiser som ger ångest över missad motion även när du är sjuk och redan mår dåligt. Våra myndigheters chattbotar upprepar om och om igen “Jag förstår inte vad du säger, försök igen” till medborgare med kognitiva utmaningar. Digitala tjänster kan direkt bidra till muskulära spänningar, rastlöshet, utmattning och koncentrationsproblem.
Det är lätt att tro att digital tillgänglighet handlar om likvärdig tillgång till information. Men tillgänglighet handlar i grunden om rätten, och förmågan, till ett värdigt liv.
Vi måste komma ihåg att en checklista som webbtillgänglighetsdirektivet endast är en liten del av detta. Vi lagstiftar inte bara för att alla ska kunna deklarera via nätet. Vi lagstiftar också för att rädda liv.
Det finns en strävan att AI ska integreras i våra sociala domäner och myndigheter, med känsliga beslut om vem som får resurser och möjligheter, och vem som nekas. Dessa system har om och om igen visat sig fördomsfulla.
Allt ifrån röstigenkänning som inte kan hantera gälla – eller mer feminina – röster, till diagnostiska system som fungerar sämre för mörkhyade människor, till rekryteringssystem som nedvärderar ansökningar från kvinnor.
Tillgänglighet är ofta utelämnat från dessa konversationer, ytterligare bevis för hur funktionsnedsättningar återigen kommer i sista hand, även i fall där det aktivt forskas och pratas om orättvisa.
AI-system ser världen utifrån den information de matas med. Om ett automatiserat rekryteringssystem saknar information om kvinnliga kandidater så kommer kvinnliga kandidater att avvika och inte kännas igen. Om samma system saknar information om människor med olika former av kommunikativa beteenden och förmågor, så kommer en stor mängd människor att nekas jobb på dessa grunder. Det är samma fördomar som vi lever med idag, men nu befästa i ett system som marknadsförs som smartare, bättre och mer objektivt.
Ett AI-system kan i värsta fall cementera fördomar och bromsa samhällsförändringar i skepnaden av att att vara överlägset. En ny typ av förtryckare.
De lagar vi har är en spegling av vår historia, vår nutid och den framtid vi vill ha. Det är vi tillsammans som kan verka för att synliggöra alla dessa risker, människor som åsidosätts och far illa. Det är vi som sätter agendan, med de arbetssätt vi förespråkar idag, som kan bli vedertagna imorgon, skapa medvetenhet och bidra till gemensamma värderingar i framtiden.
Det är bara genom att systematiskt jobba med strategiskt förutseende – att aktivt lägga tid på att förutspå så många risker som möjligt – och att involvera människor som är experter på riskerna, de som faktiskt är utsatta – som vi kan göra rätt.
Vi behöver inte bromsa utvecklingen, det kan vi inte, men
vi måste vara öppna med, och ödmjuka inför, de problem vi skapar
vi måste inkludera utsatta människor i arbetet, inte bara i tanken
vi måste ge självbestämmandet till människor att välja bort en automatiserad bedömning
vi måste agera så att de som är minst lyssnade på blir mest lyssnade på
Målbilden är att de som lever ett liv med begränsningar och utsatthet ska erbjudas ett liv med möjligheter.
————————
Så det var allt för mig den här gången. Lycka till med era samtal och arbeten nu.
June 24, 2020
Hey, your e-mail matters more than hype
There is a new e-mail provider in town and it’s an excellent opportunity to have a reasoned conversation about how to improve your e-mail management. I do not believe that decisions around your e-mail provider should be made lightly. Your e-mail address is often the hub of your online presence and your inbox is your sanctuary. Well, at least it could be.
First, let me break down why there is this nagging feeling of urgency to sign up for the HEY e-mail service and “be saved”. There are a number of biases in play that could be affecting you:
Authority bias. Basecamp founders are household names in the tech industry, and they also have friends in high places. There is no shortage of prominent advocates who are now buzzing about the HEY e-mail service. This could make the opinions hit closer to your heart.
Selective perception. When we favour information that we agree with we may avoid information that could have a negative impact. The ability to choose who can send you e-mail may sound fantastic. So much so that any peripheral concerns about accessibility, lock-in and privacy may pass you by.
Scarcity bias. Choosing to initially be invitation-only is a purposeful choice by HEY. It works. Since it targets a human weakness.
Bandwagon effect. Many people are talking about it – at least in your circles – and asking for invites. But going along with the crowd, when the choice is not required, can be harmful when it’s not in an individual’s best interest. HEY is not free.
Noble-edge effect. Products of caring companies are seen as superior. Basecamp is not just any company. They’ve done a lot of impressive work, often challenge common truthisms and generally contribute in a positive way to concepts of designing and working. This of course does not mean one has to jump when they say jump.
Speak-easy effect. Words that are easier to say are more trustworthy and valuable. Hey, I don’t need to explain this one , right?
FOMO. Fear of missing out. What if this really is the next big thing? Trust me, then it won’t die.
It may truly feel like you need the new shiny thing. And I’ll be honest, when I heard Jason Fried being interviewed by Kara Swisher on Recode Decode, HEY did sound like the best thing since sliced bread. Kara was noticeably craving for it.
And no one’s wrong to be entranced. The reason many of us are susceptible to the allurement of HEY is because the current state of e-mail really is failing many of us. We live with e-mail that needs fixing. From overload, from disarray, from mass-marketing and more.
But before we decide that HEY is the answer to that fix, I’ll encourage anyone and everyone to stop, reflect and reason. Because getting excited about something before it has proven its worth can too easily led us astray.
A completely new e-mail address
Here’s the thing. Signing up for HEY and using it as your main e-mail address really will mean that you have to change your e-mail address. In many places. Or get used to managing yet another e-mail address. While this can solve a lot of things it could also lead to more labor for you.
Will you need to maintain two e-mail addresses, and for how long? For many years if you still want that searchable archive.
Will you forward all e-mail from the old account? Then how much have you solved?
Can you migrate all your e-mail from the old account ?-The answer to that is a resounding no. You are starting fresh in this aspect.
If you’re prepared to switch e-mail address to solve your current problems with e-mail, and not bring any old e-mail with you, then you are prepared for some major changes in your e-mail management.
Remember, many reviews of HEY are going to be positive in the beginning. Everyone will have vastly less e-mail and it will naturally feel liberating. The primary reason they will have vastly less e-mail is that they are starting a new e-mail address with zero e-mails. Something that could be achieved with just about any service.
If you’re ready for the big change that a new e-mail address sets in motion, maybe you’re ready for decision-making that helps you seize more control over your inbox, rather than blindly trust another actor to know what’s best for you.
Before I walk you through that decision process, let me share som other facts about HEY that may help you stop and think some more:
Locking your e-mails inside HEY
HEY treats email in all sorts of special ways, so off-the-shelf 3rd party email apps won’t work with HEY.
— from the HEY FAQ
To use HEY you can only use their app and their website. There is no POP/IMAP access from other e-mail clients. If you ‘ve ever moved between accounts before you’ll remember this as a common way to migrate your e-mail, or reach multiple e-mail accounts from the same app.
On a sidenote: To get your e-mail out of HEY, if you don’t like it, they offer MBOX as an export format. And as long as you’ve paid for a first year of service your hey.com e-mail is yours forever to forward wherever you want. So you could pay $99 for the heck of it, if that ’s how you like to, and can, play the game.
More importantly, this closed garden means deviating from e-mail standards of structure, protocols and security. This does not have to be bad through-and-through, but should trigger questions around openness and transparency, and a wish to understand more before committing.
Accessibility
Some e-mail clients are better than others when it comes to making content accessible to people with, for example, variations in visual, sensory and auditive perception. Being able to use your own client of choice (software or online service) for e-mail can make all the difference between being able to even read it or not. This is one of several reasons the lack of POP and/or IMAP access can pose a huge problem.
All users, regardless of ability, become reliant on the HEY web client and apps. This means they need to cater to many different needs and abilities. And as it turns out, some concerning lapses in accessibility have already been uncovered:
So I’m checking out @dhh’s new HEY email service as I’m keen to get away from Gmail and like what they preach about smaller sustainable business. After a few minutes of looking, there is inexcusable accessibility issues that means I won’t recommend it or subscribe. — @NickColley
When a new tool by design excludes people who are time and time again excluded in society and communities, it’s generally a tool I do not wish to support. Even if I personally could fare well with the service, the way I voice my values is by not supporting tools that reject others – and especially people who are forced into vulnerability by not being listened to enough.
Finding old e-mail
If you’re anything like me, searching for e-mail with advanced operators is one of the ways I get by with e-mail management and working effectively with e-mail. HEY mentions little about how their search engine helps you do this. Again, remember that their search engine is all you’ve got since you can’t use another e-mail client to access your e-mail.
The rewards of being patient
HEY does introduce some nifty ideas on threads, subjects lines and notifications. I doubt that these will go unnoticed by other e-mail providers. If proven successful, they will likely be copied in some form. Should this occur, I’ll certainly acknowledge that we have HEY to thank for pushing the envelope.
Some features may already be available with other providers to some extent. In their marketing for the “Reply Later” feature, HEY writes:
You often know you need to get back to someone, but you don’t have time right now. Gmail, Outlook, and the rest, force you to come up with kludgy workarounds to deal with this (like marking an email unread so you hopefully remember to deal with it later). That’s ridiculous.
For anyone familiar with Gmail, there is a Snooze feature that allows you to accomplish what “Reply Later” does, and then some. I see people already posting on how much better designed the HEY version is. But hey, the marketing copy wasn’t really true to fact, was it?
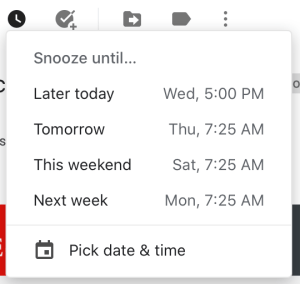 Screenshot of the Snooze feature in Gmail.
Screenshot of the Snooze feature in Gmail.Remember you’re looking to make your e-mail work for you. Keep your eye on the goal, we’re getting closer to the checklist.
Getting privacy conscious
One valid reason to avoid free Gmail is absolutely to avoid having personal data and attention traded as a product, which is often how you pay when you’re not paying with money. HEY underscores how Google’s email service relies on your data and rightfully emphasises how HEY blocks tracking pixels.
On the other hand, if privacy is a primary reason for you to choose HEY, first have a look at the sub-processors for the HEY e-mail service. A sub-processor is a data processor who, on behalf of HEY, processes the personal data of customers. These are:
Amazon Web Services. Cloud services provider.
Braintree. Payment processing services.
Google Cloud Platform. Cloud services provider.
Help Scout. Help desk software.
Mailchimp. Email newsletter service.
Sentry. Error reporting software.
TaxJar. Sales tax calculation.
Zapier. Software integration service.
It’s not a (very) long list, but may feel like a damning one depending on the trust you place in the companies on the list.
I’m not surprised by the list at all, and I’m sure the data processing agreement between HEY and these companies is by the book. It’s just one of those wake-up calls reminding us all of how many companies choose to build online software today. Relying on a network of third-party platforms is often quicker and more cost-efficient in the short term.
And when it comes to privacy, no service is stronger than its weakest link. Remember, there are other services out there blocking trackers as well.
Manage e-mail with care – A checklist for inbox improvement
Choosing HEY is a financial decision and you’ll do right by yourself if you set aside time to do your research. What HEY does well is bring to attention the importance of making choices around your e-mail that mitigate frustrations and benefit your well-being.
Decide if changing e-mail address is worth it
How much work am I willing to put into changing address where it would need to be changed? Do I send an alert to everyone in my address book and let them know? How long before I’ve just redirected all my e-mail to a new place? What is my exit strategy when I’m locked in and really don’t like it?
And if you are changing e-mail address, which in some contexts very well could prove to be a smart step, are there other services that would suit you better? This is the crucial question before taking the plunge. Because it will likely be some time before you’re prepared to move again.
I’ve listed a few services at the end of the article, most of them with a greater focus on privacy.
Decide who can e-mail you
To be fair, the opt-in feature of HEY sounds hugely appealing. Nobody could send me e-mail without my approval. Whether or not it’s a killer feature remains to be seen. It’s however not unique. Another provider is launching with the same functionality this summer, OnMail – built by the team behind Edison Mail.
If it turns out to be a hit, I expect others to follow suit with this option. Meanwhile, your current provider will offer some variant of blocking to give you more control. I encourage you to go ahead and block generously.
Opt out of seeing things you don’t need to act on or reply to
Whether you’re sticking with your current e-mail or changing to a new one you’ll do good to spend time opting out of newsletters, marketing and notifications from social platforms.
I’ve been applying this strategy extensively with all e-mails that arrive over the past six months and the effect is noticeable. Generally there are three things you may want to do:
Opt-out of things you do not want. This sounds obvious but you’d be surprised to see how many times I see people delete time and time again instead of unsubscribing.
Filter into a folder if there are senders you never want to see in your inbox but may want to find when you search
Use a separate service for newsletters you may want to read, keeping them out of your inbox. I’ve written about this in a separate post: Subscribing to newsletters the mindful way. This advice is valid even if you do choose to sign up for HEY.
Just do not use services like unroll-me to unsubscribe.
Who gets to see my e-mail address?
This is where many of us have gone wrong in the past. By sharing and posting and signing up with the same e-mail address all over the place we have set ourselves up for the misuse that we are now experiencing.
Your e-mail address is a thing of great value and more of us should probably start treating it as such.
Are you signing up for a new service that you have no prior relationship with and have no specific reason to trust? You can decide to not give them your real e-mail address. For this very purpose, I use services such as burnermail*. It will generate an anonymous e-mail and you can sign up with a unique address for every service you use. This allows you to block each address if it’s being misused.
As a bonus, trackers and advertisers will find it harder to follow your online. Your e-mail is a unique identifier that is often used to cross-reference databases to find out more about you from third parties. See what I mean about “thing of great value”?
Think again about who you want to trust with this value.
*For variants of burner mail, do an online search for “disposable e-mail” or “temporary e-mail”.
Who gets my time?
I get a huge amount of e-mail. Some are really interesting messages from students, podcast listeners, researchers, journalists and junior designers from all over the world. For me, this is why e-mail is awesome and why an opt-in solution may not work for me. It’s not always obvious who I’d want to reject as a sender. And what learnings it could cost me to do that.
Obviously replying to all these e-mails costs me as well. And sometimes there is just no time. For me, acknowledging the impossibility of responding to everyone is important. It allows me to be kinder to myself even when I feel bad about failing to reply promptly.
One thing I’ve done strictly to make myself feel better is to have a short template that I use to respond when my priorities are elsewhere. It’s most often used for e-mails where I get a lot of questions around best ways forward for a design challenge or when being asked to be interviewed for a dissertation.
Thanks for your e-mail. I am currently unable to respond to all of the many e-mails that reach me, and I will not be able to respond to yours. This is not a reflection of the content of your e-mail. This is my approach for prioritising my well-being and personal goals during periods where my capacity for attention is scarce.
Thank you again for reaching out and I wish you all the best.
Kind regards,
/Per
I reply with this and then I can archive the e-mail. In fairness this usually happens after I’ve snoozed the e-mail several times. Realising your own limits can be painful.
Full disclosure
I’ve signed up for the HEY e-mail service, gained access and started the trial. I’ve done this out of curiosity getting the better of me, for purposes of understanding the service better and getting enough experience to have an educated opinion on it. In the end it may also be a way for me to protect my brand name on a potentially popular service.
The funny things is, I just don’t know who I would tell about this e-mail address to and why I should. It seems I can get a pretty good handle of managing my e-mail without it, in an interface I am already comfortable with.
Furthermore, the seven (7!) e-mails that immediately clutter my “Imbox” (yes, that’s what they call it), with tutorials on how to use the service, seems like a disconnect from any message of simplicity. First impressions leave me… bewildered.
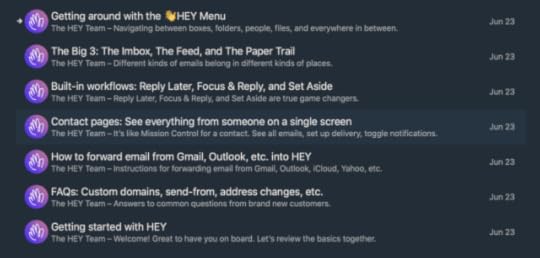 Screenshot of the 7 e-mails in my “Imbox”
Screenshot of the 7 e-mails in my “Imbox”Note that this article is not intended as a takedown of the HEY e-mail service. I’m sure it can provide value to a lot of people. Just not everyone. My text is an emotional response to an explosion of hype over the past week and I’ve made an effort to bring more thoughtfulness to the conversation. I want to highlight shortcomings and the importance of reasoned decisions when jumping on the bandwagon. No service is perfect but a strong ability to listen to reflections and feedback will likely help a company improve its products. I do believe Basecamp to be one such company. And I especially hope for a considered response to the weaknesses in accessibility .
There’s a chance HEY can change our relationship to e-mail. Then again, there’s also a big chance it won’t. But if this made you sit down and think about how you can improve your management of electronic mail, even if you don’t sign up for HEY, then perhaps the hype was worth it.
Footnote about custom domains
Eventually you’ll be able to set up your own domain with hey.com but there is no indication of how soon or far off that is. A multi-user option with this feature, targeted at businesses, is said to be ready this year.
Generally, if you own your own domain and can afford the cost of custom domains, moving between e-mail providers is an easier choice, since your e-mail address does not have to change. Obviously, only a small percentage of people enjoy this opportunity,
List of E-mail services
More and more people are waking up to the importance of privacy. Here is a list of small tech e-mail providers that raise the bar on privacy.
Fastmail (Australia)
KolabNow (Switzerland)
Mailbox (Germany)
Posteo (Germany)
ProtonMail (Switzerland)




